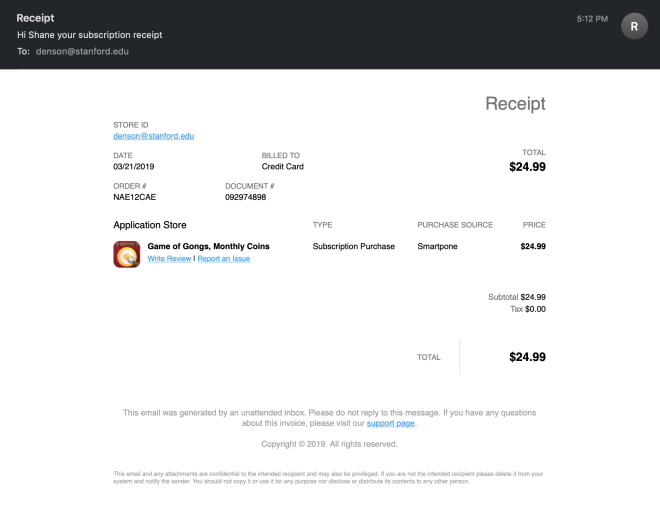
Today, I received this suspicious message on my university email account about a purchase, made on my “Smartpone,” and related to a game I don’t play. I promptly reported it as spam to Stanford IT. Within seconds, I was “rewarded” with the following message:
Thank you for reporting this suspicious message. This was a simulated phishing email sent as part of Stanford’s Phishing Awareness Program. Congratulations on successfully identifying and reporting it to us! No further action is necessary.
Yay! I guess…
Yeah, well, I think it’s kind of weird to get phishing messages from your employer, and I am getting this gamified spam on a regular basis — several “simulated” phishing messages a week.
But what is the status of a “simulated” phishing attack anyway? In this connection, I am reminded of Baudrillard on the impossibility of “simulating” a bank robbery:
Organize a fake holdup. Verify that your weapons are harmless, and take the most trustworthy hostage, so that no human life will be in danger (or one lapses into the criminal.) Demand a ransom, and make it so that the operation creates as much commotion as possible — in short, remain close to the “truth,” in order to test the reaction of the apparatus to a perfect simulacrum. You won’t be able to do it: the network of artificial signs will become inextricably mixed up with real elements (a policeman really will fire on sight; a client of the bank will faint and die of a heart attack; one will actually pay you the phony ransom).
This sounds exactly like what my employer — a major research university situated in the midst of Silicon Valley, the simulacral heart of the control society — is doing. And in their attempt to remain close to the “truth” to test the reaction of the apparatus to a perfect simulacrum, the network of artificial signs is bound to get mixed up with real elements, perhaps by design: these simulated attacks pretend towards an attempt to inoculate us against the danger, but they are also tools of control: of surveillance and, if need be, shaming (I am told by colleagues who have clicked on the links that a finger-wagging message appears and tells the user to be more careful…).
Having recently parried one of these attacks to the satisfaction of my employer, I received the usual message of congratulations. Being knee-deep in a major writing project, I may have been feeling a little humorless that day. I wrote back:
Thanks, but I am not sure that this really adds to my productivity.
I got a message back, within minutes, from someone claiming to be a human (but it seems I should have required they fill out a Captcha or click on all the stoplights in a picture or something). Anyway, this “human” wrote back a message so chilling that it sent shivers down my spine the likes of which I have rarely experienced outside of Poe or Kafka:
Hi Prof. Denson, we give up a little bit of our productivity for an increased amount of security. Thank you for the feedback and for reporting the email.